| « Back to article | Print this article |
How India's EVMs could be manipulated
In a collaborative study, a team of Indian and international experts recently revealed that the electronic voting machines used in Indian elections are vulnerable to fraud.
Even brief access to the machines, known in India as EVMs, could allow criminals to alter election results.
These research findings are at odds with claims made by the Election Commission of India, the country's highest election authority, which has maintained that weaknesses found in other electronic voting systems around the world do not apply to India's EVMs.
In 2009, the Election Commission of India publicly challenged Hari K Prasad to show that India's voting machines could be compromised. But incredibly, they did not give him access to a machine. Prasad's team managed to acquire an EVM from a source earlier this year, and soon proceeded to expose security flaws.
Prasad was arrested on August 21 for refusing to disclose the identity of the source from whom the EVM was secured for the tests.
Click on NEXT to read excerpts from the researchers' report on how India's EVM's are vulnerable
Excerpts courtesy: indiaevm.org
No way to check if EVMs are authentic
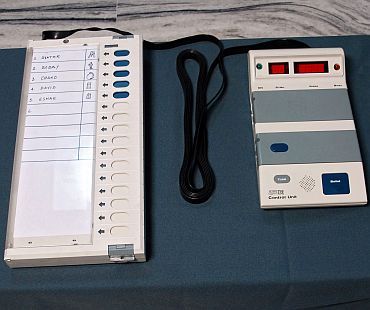
Indian EVMs consist of a ballot unit used by voters and a control unit operated by poll workers.
Voters and poll workers have no practical way to verify that the EVMs they use are authentic.
So attackers might try to build identical looking but dishonest control units or ballot units and substitute them before an election.
Since the units the researchers examined had no effective way to verify the authenticity of the units they are paired to, replacing either unit with a dishonest one would allow the attacker to alter election results, they said.
Prone to electronic, not physical tampering
The control unit displays vote totals for each candidate at the end of the election.
Prior to this study, Hari Prasad constructed a proof-of-concept look-alike EVM. He found that matching the electronic functionality was easy due to the simple design of the machine, but duplicating the plastic housing was more difficult.
For this reason, attackers may prefer to tamper with real machines (if they can get access to them) by replacing chips or entire circuit boards within the original cases, the researchers said.
Appears superior but not quite so
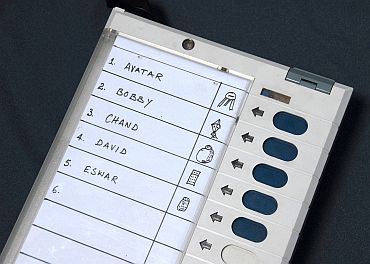
The ballot unit is used by voters, who simply press the button corresponding to the candidate of their choice.
Prior studies of electronic voting security have recommended avoiding complexity and minimising the size of the trusted computing base.
In light of this advice, India's EVMs might superficially appear to be superior to most other deployed Direct Recording Electronic voting machines.
The EVMs use a simple embedded system design, as described in the previous section, and while many other DREs rely on commodity operating systems and run election software containing tens or hundreds of thousands of lines of code, the EVM software is compact, consisting of only a few thousand instructions that run directly on the hardware.
The EVMs' minimalist design makes it more vulnerable to attacks, which could be accomplished without the involvement of any field-level poll officials, the researchers said.
Access to one EVM enough for an attack
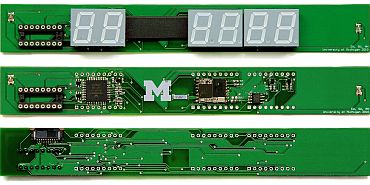
Inside the EVM is a main circuit board with the CPU and vote memory, as well as a smaller display board. This hardware has never before been subjected to detailed public scrutiny.
The control unit contains the main circuit board. The centrepiece is the EVM's CPU, a Renesas H8/3644-series microcontroller driven by an 8.8672 MHz crystal oscillator. The CPU is custom manufactured with the election software permanently recorded in an internal mask ROM.
This prevents the software from being electronically reprogrammed. Also on the main circuit board are the switches for the buttons on the face of the device, a buzzer1, two EEPROM chips used for non-volatile storage of vote data, the display board connector, and the connector for the ballot unit.
There are nearly 1.4 million EVMs in use throughout the country, and criminals would only need access to one of them to develop working attacks. Dishonest insiders or other criminals would likely face less difficulty than the team did in obtaining such access.
EVMs lack cryptographic mechanism
Attackers might try to substitute look-alike CPUs containing software that counts the votes dishonestly. Other than the firmware, the CPUs are a commodity part, so obtaining and programming identical hardware would be straightforward.
The EVM designers could have made such attacks more difficult by building a cryptographic mechanism for identifying the original CPUs such as a challenge-response protocol based on a secret contained in the original firmware.
Since they did not, this attack would only require creating new software with nearly identical functionality to the original, a task that is relatively easy because of the EVMs' simple design.
Wireless EVM fraud is possible
The real chips could be swapped with dishonest ones in the supply chain or by attackers with access to the assembled machines. Prior to assembly, they could be swapped by corrupt employees at the chipmakers or the couriers that transport them.
The researchers developed an application that runs on an Android mobile phone and wirelessly tells the dishonest display which candidate should receive the stolen votes.
It sent a short message to the dishonest display via RFCOMM indicating the favoured candidate and the proportion of votes to grant that candidate. The application verified success by waiting for an acknowledgment from the dishonest display.
Their application did not use any special Android features. So it could be ported to any smartphone platform that supported Bluetooth RFCOMM Protocol, such as the iPhone or Windows Mobile.
Pocket-size device can tamper an EVM
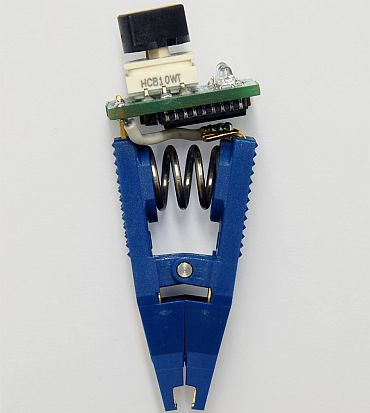
The researchers also developed a demonstration attack device that clips on to the memory chips inside the EVM and steals votes.
It attached directly to the memory chips that store the votes in the control unit.
The device fits in a shirt pocket. So an attacker who forcibly took control of an EVM could use it to stuff the electronic "ballot box" with any number of votes.
Internally, the EVM records votes in the order in which they were cast. The device can be used to extract these records.
An attacker who observed the order in which voters used the machine could then determine which candidate each voter selected.
Stealing at convenience
To use the device, the attacker opens the EVM control unit and connects a jumper wire to the CPU to hold it in reset.
Next, he powers on the machine and clips the device to one of the EEPROM chips.
When the "Done" LED lights up, the attacker disconnects the device and repeats the process for the second memory chip.
To steal votes, the attacker indicates his favoured candidate using the rotary switch.
All it takes is a laptop with a serial cable
The rotary switch selects a number from 0 to 9, and the attacker can use it to pick a favoured candidate in any of the first nine ballot positions, which normally include the major national parties.
When the switch is set to positions 1-9, the clip-on device executes a vote-stealing programme.
The program runs in two passes: first, it reads the vote data and calculates how many votes to steal from each candidate; second, it rewrites the list of votes, stealing votes as calculated in the first phase.
An attacker could also use this clip-on device to violate the secret ballot. The device can be connected to a laptop computer with a serial cable, and, when the rotary switch is set to position 0, it awaits commands to read or write the EEPROM. This allows the attacker to download the machine's ordered vote records to the laptop.
The flip-side to having a secret software
The processor in the EVM is designed so that the election software is hard to read out. Election officials claim this is a security feature, but it makes it difficult even for the authorities to verify that the correct software is in the EVMs.
Even if the correct software is there, it is risky to design a voting system such that its security depends on keeping the program secret.
If attackers do come to know about the secret software, there is no way to recover except by changing to new software -- an expensive and time-consuming proposition.
Physically tampering with a large fraction of EVMs might be difficult, as there are so many in use. However, in close races, an attacker might be able to change the election outcome by tampering with only a few machines.
A small number of tightly contested seats often determine which party holds a majority in Parliament, so a national-level attacker could focus on tampering with machines in these districts.
Seals are extremely weak
Poll workers attempt to protect the EVMs from tampering using an elaborate system of seals placed over different parts of the machine at various points in the election cycle.
However, these seals are extremely weak, consisting of stickers, strings, melted wax and plain paper labels.
None of the material is difficult to obtain or manipulate.
Even if the seals were difficult to attack, responding to broken seals presents additional challenges for election officials.
What should officials do if, after an election but before votes are counted, they discover that a large number of control unit seals have been broken? This could be evidence of a memory manipulation attack like the one demonstrated, which would leave no other visible traces, so officials might decide to discard all votes from machines with broken seals.
However, this would create an even easier, low-tech attack opportunity: a dishonest insider or other criminal could simply break the seals on control units at polling places where voters were likely to favour an opponent.