| « Back to article | Print this article |
How Pakistan, China get sensitive information on India
Government officials pin the blame on the vulnerable anti-virus solutions for failing to prevent malware from corrupting the system.
When an employee of the state-run Bharat Sanchar Nigam Limited (BSNL) got a genuine-sounding call from an Indian army officer on February 19, he never imagined the caller would in fact be a Pakistan intelligence operative (PIO).
The BSNL staff passed on the information the caller, who he thought had dialled from the Army headquarters in Delhi, asked for.
The imposter had a free run until it was detected that the call came from Pakistan. This incident sent alarm bells ringing, but the top brass of India's elite intelligence wing was not amused. Reason: the officials had encountered similar situations in the past as well.
Although such an attempt is akin to firing a shot in the dark, it is one of the most commonly used tricks of the trade to con gullible people into parting information.
Spoofing is a way of concealing one's real identity and assuming a fake one. What caught the attention of the intelligence officials was the level of penetration that foreign spooks were able to do this time.
Click NEXT to read more...
How Pakistan, China get sensitive information on India
For instance, a series of emails were exchanged between the PIO and the unsuspecting BSNL employee, which culminated in installation of malware on BSNL servers.
Apparently, BSNL hosts India's largest database of telephone numbers and call records because except in Delhi and Mumbai, almost all government telephone numbers operate on BSNL networks.
"Spoofing is a routine exercise, but this particular incident was unique and generated much attention. The spooks managed to install a malware that corrupted some data," says a top-ranking official who was part of the crack team that attended to the situation.
He adds the malware was flushed out but not before it caused limited damage. "It could have been worse."
According to the official, despite many attempts, neither the Chinese nor Pakistani agencies have been able to access critical information concerning India.
Even as the security establishment was still grappling with the BSNL incident, two days later a similar attempt was made on the elite National Security Guard (NSG).
Click NEXT to read more...
How Pakistan, China get sensitive information on India
The PIOs had ostensibly called the agency headquarters in New Delhi to elicit information about the movement of its commandos in the wake of the Hyderabad serial blasts that killed 16 people and injured 117 on February 21.
That day, the agency's blast assessment team left Delhi on a special aircraft at 9.30 PM and reached Hyderabad after two hours.
In the ensuing months, more such incidents came to light. One report suggested the President's Secretariat was spoofed. With these incidents becoming a regular affair, they also exposed the vulnerability of critical infrastructure to such attacks.
Eventually, it forced the sparring but powerful arms of the government to reconcile under one roof to find a solution.
In one such brainstorming meeting, which was chaired by the deputy National Security Advisor (NSA) and attended by the Intelligence Bureau (IB), Research & Analysis Wing (RA&W), Computer Emergency Response Team (CERT)-India, National Technical Research Organisation (NTRO), defence forces, and the Department of Telecommunication (DoT), the top brass conceded that Indian servers and data centres are not only being targeted from outside, but are also used to carry out attack targets abroad.
Click NEXT to read more...
How Pakistan, China get sensitive information on India
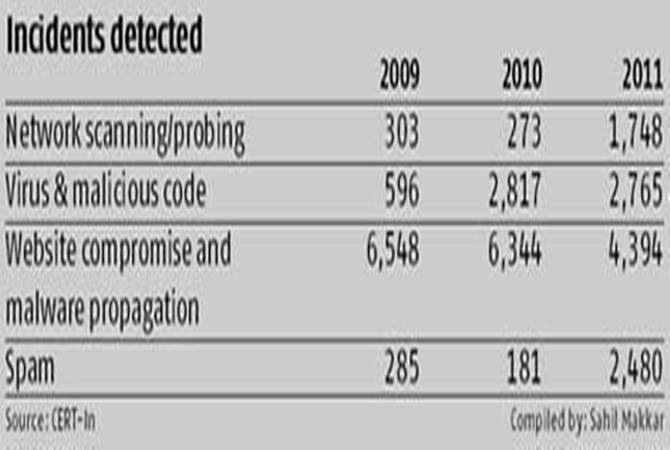
In fact, such incidents are on the rise. For instance, open proxy server systems, which are used to bypass network controls, have registered a significant growth.
CERT-In identified 2,987 open proxy servers in 2012, up from 2,826 in 2011. Around 1,000 have been identified till July this year. These proxy servers are a major source of spam on the Internet and are used to attack other servers as well.
Government officials pin the blame on the vulnerable anti-virus solutions for failing to prevent malware from corrupting the system.
"National Informatics Centre (NIC) brought out that servers are client-based. Commercial anti-virus solutions are either not updated or not effective… home grown trusted solutions is an emerging need. The case of Linux-based machines is even more problematic and upload of web shell can't be detected," reads the minutes of the meeting held on May 2.
Business Standard has reviewed the minutes. "Almost all the anti-viruses have weakness and limitations," the minutes add. To be clear, the security demands of government and private individuals are different and should not be equated.
Jiten Jain, a cyber expert and researcher on Chinese spyware, says most of the anti-virus programs are not of much help. They can only ward off threats, which are already identified.
Click NEXT to read more...
How Pakistan, China get sensitive information on India
"What if a new malware is generated using new codes or signatures every time? Then there is no central repository of threats detected by each individual software provider. The companies do not share data with one another," he says.
Lack of trusted indigenous products has further compounded the problem.
According to Akash Agarwal, country head of EC-Council, which certifies course in ethical hacking, hardly anybody in the country is making anti-virus software.
"Indians do it for other countries. There is no guarantee the foreign service provider will not override the systems in guise of anti-virus. There has to be people who can cater to demands of government."
In fact, the Centre for Development of Advanced Computing (C-DAC) - Hyderabad has developed a malware detection system and it is undergoing logical tests. The government expects that once the system is in place, it will boost India's cyber protection capability manifold.
Jagannath Patnaik, director (channel sales - South Asia) at Kaspersky Lab, however tries to dismiss apprehensions about anti-virus companies. "We have the fastest updates in the industry and Kaspersky Lab's response time to threats is much quicker than the competition. Any standard anti-virus program would need at least four hours to block the more than 200,000 malicious programs that emerge every day," he says in an email response.
Click NEXT to read more...
How Pakistan, China get sensitive information on India
Around 30 anti-virus brands operate in India with a market size of nearly $300 million.
However, this is not sufficient. On May 2, the government agreed that there is a need of hardening the NIC networks, which host almost all government and state websites.
At the same meeting, the deputy NSA directed the NTRO and CERT-In, both of which have the mandate to mitigate cyber threats and launch investigations, to share details of malware detection with other agencies.
IB has also issued an alert against all-out attempts of PIOs to scoop information from India's defence establishments and other strategic organisations. It believes PIOs have employed the twin strategy of spoofing and snooping by installing malware.
"The Inter State Intelligence (ISI) operatives are targeting the Indian Railways, banks, and serving and retired employees and civil contractors working for Military Engineering Services (MES) to collect sensitive and defence-related information," The Hindu, quoting the IB alert, reported this month.
Click NEXT to read more...
How Pakistan, China get sensitive information on India
"They (PIOs) have also been making telephone calls under assumed identities by using spoofed numbers to various CPMFs (central paramilitary forces), railways, banks etc. They (PIOs) have succeeded in ferreting out sensitive information from the persons attending these calls. IB has been regular in highlighting the stratagem of PIOs using fake identities."
Senior officials in the Union home ministry say they regularly issue circulars about do's and don'ts to government employees from sharing sensitive information with others. In one of these circulars, reviewed by Business Standard, the home ministry advises government officials not to use telephone systems which are exposed to the external environment, mobile or any other type, for dissemination of classified nature.
The government believes heightened awareness among its staff could be the only effective way to counter attempts of foreign agencies.
HIGH ALERT
Instructions to government officials on sharing information over telephone calls against the backdrop of spoofing and espionage
* Telephone systems, which have any part of their network exposed to external environment, should not be used to disseminate classified information
* Classified Information should be restricted to organisation's own secure internal communication network
* Telephone instruments should have the facility to identify the caller
* As information security principle, confidential matter should never be discussed or transacted over phone. If circumstances necessitate, persons attending to a telephone call should identify the caller beyond all reasonable doubt before parting information
* In case, the identity of the caller is not established beyond all reasonable doubt, the person should be asked for his contact details
* The contact details should be immediately verified by calling back, as the most effective countermeasure.
* If the caller tries to give reasons that only he can contact the recipient of the call due to technical reason. It should raise the strong suspicion that is a spoofed call
* If it comes to the notice that intruder has managed to secure information, the matter should be immediately reported to seniors for remedial measures